Have you ever thought about how all those smart gadgets around us, the ones that make our homes or businesses run a bit smoother, actually connect and share their information? It's pretty fascinating, is that. From smart thermostats to industrial sensors, these devices are constantly talking, sending data, and sometimes, they need a little help or a quick check-in from afar.
The internet of things, or IoT, is, in a way, like a huge, interconnected web of everyday objects. These objects, embedded with tiny sensors and software, are able to talk to each other and to the cloud without us even lifting a finger. According to Lewis, IoT is the bringing together of people, processes, and technology with connectable devices and sensors, all to enable remote monitoring and status updates, which is quite handy.
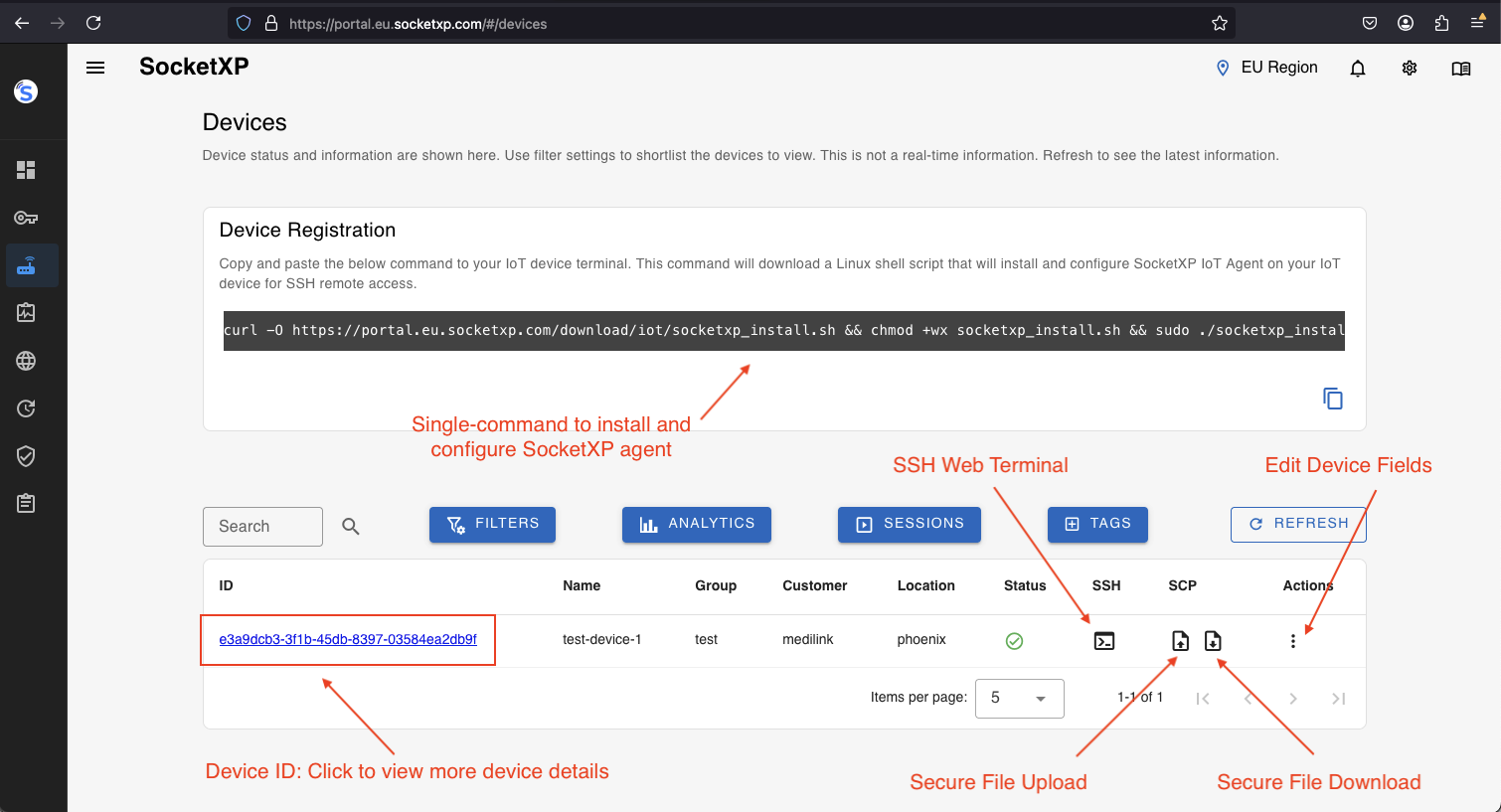
So, when you have these devices scattered about, perhaps in different buildings or even different cities, getting to them to fix something or pull some data can become a real head-scratcher. That's where something like iot ssh over ssh steps in, offering a clever and secure way to reach out and touch your devices, no matter where they are, so it's almost a lifesaver for remote management.
Table of Contents
- What is IoT, Anyway?
- Why Do IoT Devices Need Remote Access?
- SSH: A Trusted Friend in IoT Security
- Getting to Know iot ssh over ssh
- The Big Gains from Using iot ssh over ssh
- Setting Up Your iot ssh over ssh Connection: A Simple Guide
- Keeping Things Safe: Best Practices for iot ssh over ssh
- Common Roadblocks and How to Get Past Them
- What Comes Next for iot ssh over ssh
- People Often Ask About iot ssh over ssh
What is IoT, Anyway?
The internet of things, or IoT, is a network of interrelated devices that connect and exchange data with other IoT devices and the cloud, so it's a pretty big concept. These devices are typically embedded with sensors, software, and other technologies, allowing them to collect and send information. It's like giving everyday items a voice and a way to share what they "see" or "feel," which is pretty neat, actually.
The term IoT, or internet of things, refers to the collective network of connected devices and the technology that helps them talk to each other and to the cloud, as well as between themselves. It's a vast network where physical objects, like your smart fridge or a factory machine, can interact and exchange data, often without any human involvement, you know. This idea was first brought up by computer scientist Kevin Ashton, which is a bit of history there.
IoT devices are physical objects embedded with sensors that communicate with computers, allowing the physical world to be digitally watched or controlled. The IoT connects ordinary objects to other objects or applications in the cloud, making them "smart"—intelligent and interactive. The system relies on the internet protocol (IP) and transmission control protocol (TCP), which together give the rules for devices to connect, basically. So, in a way, it's about making our surroundings more responsive and connected, which is really something.
Why Do IoT Devices Need Remote Access?
Imagine having hundreds, or even thousands, of tiny sensors spread across a large farm, monitoring soil moisture or crop health. Going to each one physically for updates or fixes would be a massive chore, very time-consuming, actually. This is where the ability to access these IoT devices from a distance becomes not just useful, but absolutely necessary, you see.
Remote access allows someone to check on a device's status, update its software, or troubleshoot a problem without having to be right there next to it. For businesses, this means less travel time, lower operational costs, and quicker responses to issues. Think about a smart city infrastructure; you can't send a technician to every street light or traffic sensor whenever there's a minor glitch, can you?
This kind of remote control is also important for data collection. Many IoT applications are about gathering information over time to spot trends or make better decisions. Being able to pull that data securely and efficiently from anywhere is a big plus, and it truly helps with managing large-scale deployments. Without remote access, the very promise of IoT — connecting ordinary objects to make them smart and interactive — would be much harder to achieve, you know.
SSH: A Trusted Friend in IoT Security
When we talk about getting into a device from afar, especially one that might be handling important information, security is the first thing that should come to mind. That's where SSH, or Secure Shell, enters the picture. It's a network protocol that gives you a secure way to operate network services over an unsecured network, which is very important.
Think of SSH as a private, encrypted tunnel through the public internet. When you use SSH to connect to a device, all the information passing back and forth, like commands you send or data you receive, is scrambled so that no one else can easily read it. This makes it incredibly hard for bad actors to snoop on your connection or tamper with your devices, which is a huge relief, basically.
For IoT devices, many of which might have limited processing power or memory, SSH is a good choice because it's relatively lightweight yet provides strong security. It helps to keep unauthorized people out and ensures that the data going to and from your devices stays private. This is a crucial piece of the puzzle for keeping your IoT setup safe and sound, especially in today's world where data breaches are, unfortunately, a common worry.
Getting to Know iot ssh over ssh
So, we've talked about IoT and how SSH helps keep things secure. Now, let's put them together: iot ssh over ssh. This phrase describes a method where you use an SSH connection not just to log into a device directly, but to create a secure tunnel through which other network traffic can pass, so it's a bit like a secret passageway.
Imagine your IoT device is behind a strict firewall or on a private network that isn't directly reachable from the internet. You can't just connect to it using a standard SSH login. With iot ssh over ssh, you set up an initial SSH connection to an intermediary server, often one that *is* accessible from the internet. Then, through that secure SSH connection, you create another "tunnel" that reaches back to your hard-to-reach IoT device, which is pretty clever, actually.
This technique is particularly useful for managing many IoT devices that might be deployed in various locations, perhaps without public IP addresses or behind complex network setups. It allows you to centralize your access point while still maintaining strong encryption and authentication for each connection. It's a way to punch through network barriers safely, making remote management much more practical and secure, you know.
How iot ssh over ssh Works Its Magic
The core idea behind iot ssh over ssh involves SSH tunneling, sometimes called SSH port forwarding. There are a few kinds, but for remote IoT access, reverse SSH tunneling is often the star of the show. With this method, your IoT device, which is usually the one behind a firewall, initiates an SSH connection *out* to a publicly accessible server, which is a key difference.
Once that initial connection is made from the IoT device to the public server, the device requests that a specific port on the *public server* be "forwarded" back to a port on the *IoT device itself*. This means that any traffic sent to that specific port on the public server will then be securely sent through the established SSH tunnel directly to the IoT device, which is very handy. It's like the IoT device is telling the public server, "Hey, when someone knocks on this door, send them straight to me through our private line," you see.
For example, if your IoT device has a web interface on port 80, you could set up a reverse SSH tunnel so that accessing `public-server-ip:8080` on your computer would actually connect you to `iot-device-ip:80` through the secure tunnel. This method is incredibly powerful because it lets you bypass network address translation (NAT) and firewalls that would normally block direct incoming connections to your IoT devices. It creates a secure, on-demand pathway, making remote management much more straightforward, basically.
The Big Gains from Using iot ssh over ssh
Using iot ssh over ssh offers some really compelling advantages, especially when you're dealing with a large number of distributed devices. One of the biggest wins is, without a doubt, the enhanced security. Since all traffic goes through an encrypted SSH tunnel, your commands, data, and device access are protected from eavesdropping and tampering, which is pretty reassuring, you know.
Another major benefit is the ability to bypass tricky network configurations. Many IoT devices are deployed in environments where they don't have a public IP address or are behind firewalls that you can't easily configure. iot ssh over ssh lets your devices "call out" to a central server, establishing a connection that you can then use to "call back in," effectively getting around those network barriers, which is very clever, actually.
This approach also centralizes access management. Instead of needing to set up individual network rules or VPNs for each device location, you can manage access to your IoT fleet through a single, well-secured intermediary server. This simplifies administration, reduces complexity, and makes it easier to scale your IoT operations. Plus, it often means less hassle for your IT team, which is always a good thing, you know. It provides a consistent and reliable way to connect, even when network conditions might be a bit challenging.
Setting Up Your iot ssh over ssh Connection: A Simple Guide
Getting iot ssh over ssh up and running might seem a bit complex at first glance, but it's pretty manageable once you break it down. You'll typically need three main things: your IoT device, a publicly accessible intermediary server (often called a "jump host" or "bastion host"), and your local computer from which you'll manage everything, you know.
First, on your IoT device, you'll need to make sure SSH client software is installed. Many Linux-based IoT platforms, like Raspberry Pi, come with it pre-installed. You'll then configure your IoT device to initiate an SSH connection to your public server. This connection will include a command to set up a reverse tunnel. For example, you might use something like `ssh -R 8080:localhost:80 user@your_public_server_ip`, which tells the public server to forward traffic from its port 8080 to the IoT device's port 80, so it's a direct line.
It's a good idea to use SSH key-based authentication for this connection, rather than passwords, for better security. Generate an SSH key pair on your IoT device and copy the public key to the `authorized_keys` file on your public server. This way, the connection can be established without needing to store or transmit passwords, which is a much safer way to go, apparently.
Once the IoT device establishes that reverse tunnel to the public server, you can then, from your local computer, connect to the public server. From there, you can access the forwarded port to reach your IoT device. So, if you set up the tunnel as `8080:localhost:80`, you would then connect to `your_public_server_ip:8080` from your local machine, and that connection would be securely routed through the tunnel to your IoT device's port 80, giving you access, you know. This setup makes it very convenient to manage devices that are otherwise hard to reach.
For persistent connections, especially for devices that might reboot or lose network connectivity, you can use tools like `autossh`. This little utility automatically restarts SSH sessions and tunnels if they drop, making your remote access much more reliable. It ensures that your IoT devices remain accessible without constant manual intervention, which is very helpful for long-term deployments, you know. Setting this up carefully means your remote access will be stable and ready when you need it.
Keeping Things Safe: Best Practices for iot ssh over ssh
While iot ssh over ssh is inherently secure, there are still some important steps you should take to make sure your setup is as strong as it can be. First and foremost, always use SSH key-based authentication. Passwords can be guessed or brute-forced, but SSH keys, especially strong ones, are much harder to crack. Make sure your private keys are kept very secure on your local machine and never shared, you know.
Another key practice is to limit the privileges of the SSH user account on your IoT devices. This means creating a dedicated user for SSH access that only has the minimum permissions needed to do its job. If, by some chance, an attacker does gain access to that account, their ability to do harm will be severely restricted, which is a very good safeguard, you see.
It's also a good idea to restrict SSH access on your public server to only specific IP addresses. If you know you'll only be connecting from your office or home network, you can configure your server's firewall to only allow incoming SSH connections from those known IP addresses. This adds another layer of defense, basically making it much harder for unauthorized people to even attempt to connect, you know.
Regularly update the software on both your IoT devices and your public server. Security vulnerabilities are discovered all the time, and software updates often include patches for these issues. Keeping everything current helps to close potential backdoors and keeps your system protected against the latest threats, which is pretty vital. Also, monitor your server's logs for unusual activity; early detection can prevent bigger problems down the line, so it's worth checking often.
Common Roadblocks and How to Get Past Them
Even with a solid plan, you might run into a few bumps when setting up iot ssh over ssh. One common issue is network connectivity itself. IoT devices often rely on Wi-Fi or cellular connections, which can be unstable. If the connection drops, your SSH tunnel will break, too it's almost a given. Using tools like `autossh` can help here, as they automatically try to re-establish the connection, which is very helpful.
Another challenge can be managing a large number of devices. Setting up individual SSH tunnels for each device manually can become quite tedious and error-prone. For larger deployments, you might want to look into more advanced management tools or scripts that can automate the process of establishing and maintaining these tunnels, which saves a lot of time, basically. Some commercial IoT platforms also offer built-in secure remote access features that might simplify things further.
Firewall configurations on both the IoT device's network and the public server can also cause headaches. You need to make sure that outbound connections from the IoT device are allowed, and that the specific port you're forwarding on the public server is open for incoming connections from your local machine. Sometimes, it's just a matter of checking those firewall rules carefully, you know. Patience and careful debugging are your best friends here, honestly.
What Comes Next for iot ssh over ssh
As IoT continues to grow, the need for secure and reliable remote access methods like iot ssh over ssh will only become more important. We're seeing more devices come online every day, and managing them all effectively and safely is a big task. This method provides a very practical solution for many current challenges, you know.
Future developments might include even more streamlined ways to deploy and manage these SSH tunnels, perhaps through cloud-based services that simplify the intermediary server setup. There could also be improvements in how resource-constrained IoT devices handle persistent SSH connections, making them even more stable and efficient. The underlying principles of strong encryption and secure tunneling, however, are likely to remain a cornerstone of IoT security for a long time, basically.
The ability to securely reach out to a device, no matter its location or network setup, is a game-changer for many IoT applications, from smart agriculture to industrial automation. As of late 2023, iot ssh over ssh remains a powerful and trustworthy technique for those who need fine-grained control and top-notch security for their connected things, which is pretty significant.
People Often Ask About iot ssh over ssh
Is iot ssh over ssh truly secure for sensitive data?
Yes, it is very secure when set up properly. SSH uses strong encryption and authentication methods, meaning that data transmitted through the tunnel is protected from being read or tampered with by unauthorized parties. Using SSH keys and strong security practices further enhances this protection, you know.
Can I use iot ssh over ssh with any IoT device?
Generally, you can use it with any IoT device that runs a Linux-based operating system or has an SSH client available and enough processing power to maintain the connection. Devices like Raspberry Pis, BeagleBones, and many industrial IoT gateways are good candidates, basically. Very small, deeply embedded devices might struggle, though.
What if my IoT device's internet connection is unreliable?
An unreliable internet connection can indeed cause the SSH tunnel to drop. To deal with this, you can use tools like `autossh` on your IoT device. `autossh` is designed to monitor an SSH connection and automatically restart it if it goes down, making your remote access much more resilient, which is very helpful, you know.
To learn more about IoT security basics on our site, and for further reading on secure remote access methods, you might want to check out this page about IoT security best practices.
For more detailed technical information on SSH tunneling and its various applications, you could look at resources from reputable cybersecurity organizations, like the National Institute of Standards and Technology (NIST) or similar bodies. Their publications often provide in-depth guides and recommendations for secure network protocols, which is very useful, you know. For example, you can often find great technical guides on secure shell on sites like SSH.com's Academy.
Thinking about how you manage your connected devices? Consider giving iot ssh over ssh a try. It really does offer a dependable way to keep your IoT fleet secure and accessible, no matter where they are. It's a smart step for anyone serious about remote device management in today's connected world.

Detail Author:
- Name : Murray Franecki
- Username : lbernhard
- Email : boyer.lucienne@hotmail.com
- Birthdate : 1994-08-03
- Address : 9877 Bailey Club Suite 189 South Kennithport, VA 32250
- Phone : +18562581901
- Company : Bradtke, Rohan and Dare
- Job : Animal Husbandry Worker
- Bio : Voluptatem non doloribus sint. Vel voluptates ut qui qui fugiat repellat aut harum. Veritatis fugiat quia cumque doloremque. Enim fugiat quasi occaecati eligendi omnis quis ea.
Socials
twitter:
- url : https://twitter.com/pierce_turner
- username : pierce_turner
- bio : Et praesentium eos non tenetur placeat. Sit accusamus quasi ut nihil cum in et. Doloremque eius iusto laborum quia molestias culpa molestias.
- followers : 5339
- following : 835
linkedin:
- url : https://linkedin.com/in/turner2018
- username : turner2018
- bio : Dolores magnam eum corrupti ad.
- followers : 2474
- following : 2906
tiktok:
- url : https://tiktok.com/@pierce_official
- username : pierce_official
- bio : Et voluptatem ut sunt occaecati voluptatem.
- followers : 1349
- following : 2797
facebook:
- url : https://facebook.com/turner1981
- username : turner1981
- bio : Aut cumque velit voluptatem est inventore quia dolorem possimus.
- followers : 6622
- following : 1355

